You know the drill. One day it's a firewall update. The next day there's a failed backup that needs attention. Then someone mentions a suspicious email, and suddenly you're knee-deep in incident logs trying to figure out what happened. Welcome to IT whack-a-mole, the never-ending game that defense suppliers play when they try to manage CMMC compliance in-house.
Here's the thing: you didn't get into the defense business to become a cybersecurity expert. You're here to build parts, provide services, and support our nation's warfighters. But CMMC 2.0 Level 2 compliance demands continuous monitoring, constant vigilance, and a level of IT operations expertise that most small to medium businesses simply don't have on staff.
That's where CPE Level 2 changes everything. We handle the heavy lifting so you can focus on what you do best.
The Real Problem: Compliance Isn't a One-Time Event
Let's be honest. A lot of companies think CMMC compliance is like passing a driving test, study up, pass the exam, and you're good to go. That couldn't be further from the truth.
CMMC 2.0 Level 2 requires ongoing monitoring and reporting. We're talking about:
- Continuous security event monitoring across your entire environment
- Real-time log analysis to catch threats before they become incidents
- Regular configuration assessments to ensure nothing has drifted out of compliance
- Network traffic monitoring for anomalies and potential breaches
- Host-level security management on every single endpoint
For a company with a dedicated IT team of maybe one or two people? That's an impossible ask. And hiring a full cybersecurity operations staff? We're talking six figures minimum, per person, per year.
Enter Managed Operations with CPE Level 2
Here's what makes CPE Level 2 different from every other compliance solution out there: we don't just set you up and walk away. We stick around and actually run the thing.
When you deploy CPE Level 2, you're getting a fully managed cybersecurity environment. That means Planet Security's team of experts is constantly watching over your systems, handling the day-to-day security operations that CMMC demands.
No more whack-a-mole. No more 2 AM alerts that you don't know how to handle. No more wondering if that weird log entry is a false positive or an actual breach in progress.
SIEM Monitoring: Your 24/7 Security Operations Center
Let's talk about Security Information and Event Management (SIEM), because this is where most DIY compliance efforts fall apart.
A proper SIEM solution collects logs from every device, application, and network segment in your environment. It correlates events across multiple data sources. It applies threat intelligence to identify malicious activity. And it generates alerts when something looks wrong.
Sounds great, right? Until you realize that a typical SIEM generates thousands of events per day. Someone has to review those events. Someone has to investigate the alerts. Someone has to know the difference between a legitimate threat and normal network noise.
With CPE Level 2, that someone is us. Our security operations team monitors your SIEM around the clock. We analyze the events. We investigate the alerts. And when something needs your attention, we tell you exactly what's happening and what to do about it.
This is what actual managed compliance looks like.

Network Compliance: Keeping Your Perimeter Locked Down
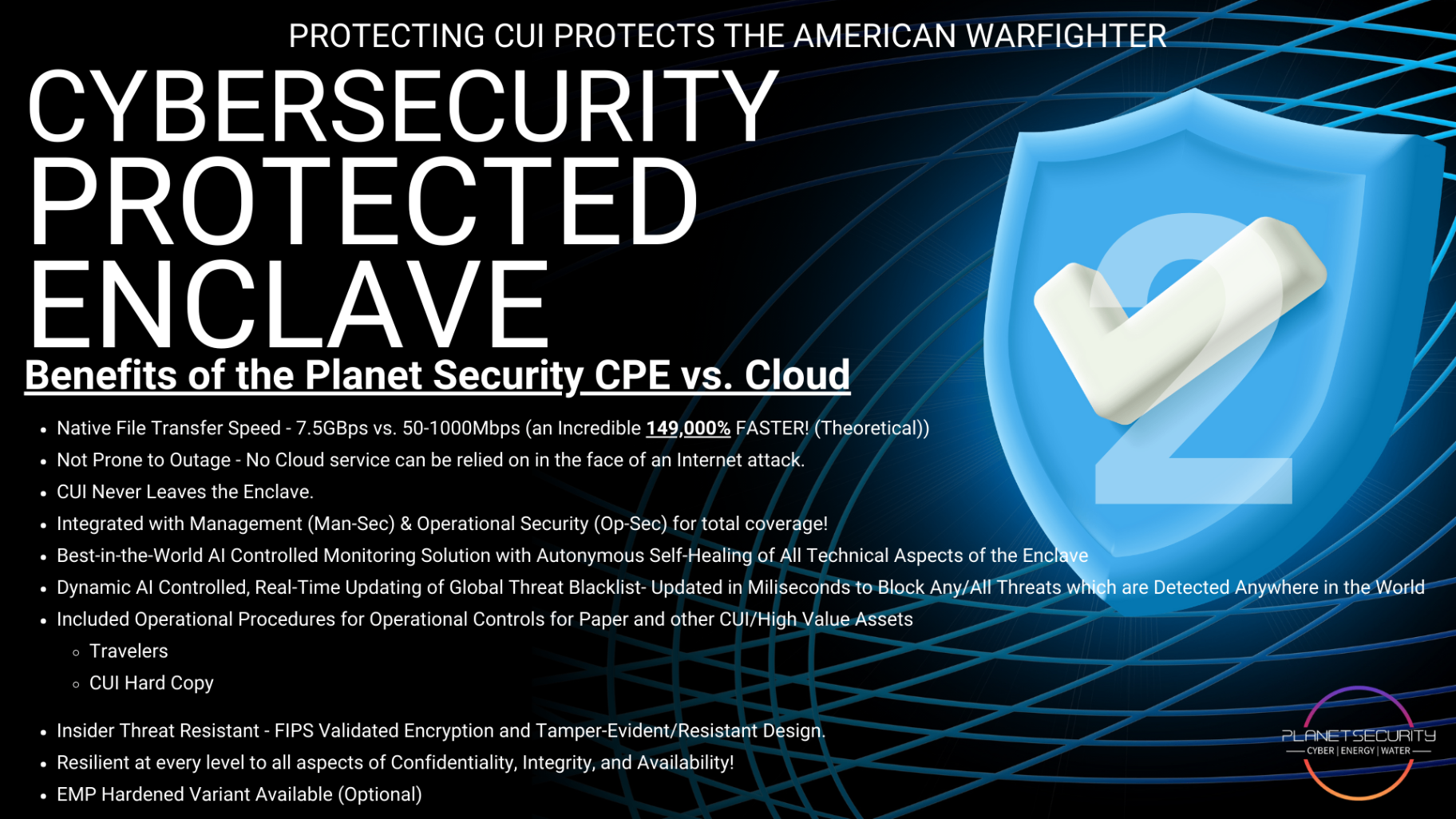
Your network is the backbone of your entire operation, and it's also the front line of your cybersecurity defense. CMMC 2.0 Level 2 has specific requirements for how your network must be configured, monitored, and maintained.
We're talking about:
- Proper network segmentation to isolate CUI from general business traffic
- Firewall rules that actually make sense and don't have gaping holes
- Intrusion detection that catches malicious traffic in real-time
- Regular vulnerability assessments to identify weaknesses before attackers do
- DNS filtering to block known malicious domains
When you try to manage this yourself, things inevitably slip through the cracks. A firewall rule gets added for a "temporary" project and never removed. Someone plugs in an unauthorized device. A vulnerability goes unpatched because nobody noticed the update.
CPE Level 2 eliminates these problems. Our team maintains your network configuration to ensure continuous compliance. We handle patching and updates. We monitor for unauthorized changes. And we conduct regular assessments to verify that everything is still locked down tight.
Learn more about our security-enabled firewalls and how they integrate with the CPE Level 2 environment.
Host Configuration: Every Endpoint, Every Time
Here's a compliance headache that keeps IT managers up at night: endpoint configuration management.
Every workstation, every laptop, every server in your CUI environment needs to be configured according to strict security baselines. We're talking about hundreds of individual settings, password policies, audit configurations, service hardening, application whitelisting, encryption settings, and on and on.
And it's not enough to configure them once. Users make changes. Software updates reset configurations. Drift happens. Before you know it, half your endpoints are out of compliance and you don't even realize it.
With CPE Level 2, we deliver endpoints that are hardened from day one with over 900 security configurations. But more importantly, we continuously monitor for configuration drift and remediate issues before they become compliance problems.
The Full Managed Operations Package
Let's break down exactly what you get with CPE Level 2's managed operations:
Security Monitoring & Response:
- 24/7 SIEM monitoring by trained security analysts
- Real-time threat detection and alerting
- Incident response guidance when issues arise
- Monthly security reports for your records
Network Management:
- Continuous network compliance monitoring
- Firewall management and rule optimization
- Regular vulnerability scanning
- Network segmentation maintenance
Host Management:
- Endpoint configuration monitoring
- Security patch management
- Backup verification and management
- Anti-malware updates and monitoring
Compliance Support:
- Ongoing documentation maintenance
- Audit preparation assistance
- vCISO services for strategic guidance
- Regular compliance health checks
All of this is included in your CPE Level 2 subscription. No surprise bills. No additional per-incident fees. No trying to figure out which vendor handles what.
Why Managed Operations Matter for Your Business
Let's get real for a second. You have a business to run. You have contracts to fulfill. You have employees depending on you. You have customers counting on your products and services.
Every hour you spend playing IT whack-a-mole is an hour you're not spending on your actual mission. Every dollar you pour into building an in-house security operations capability is a dollar that's not going into R&D, production, or growth.
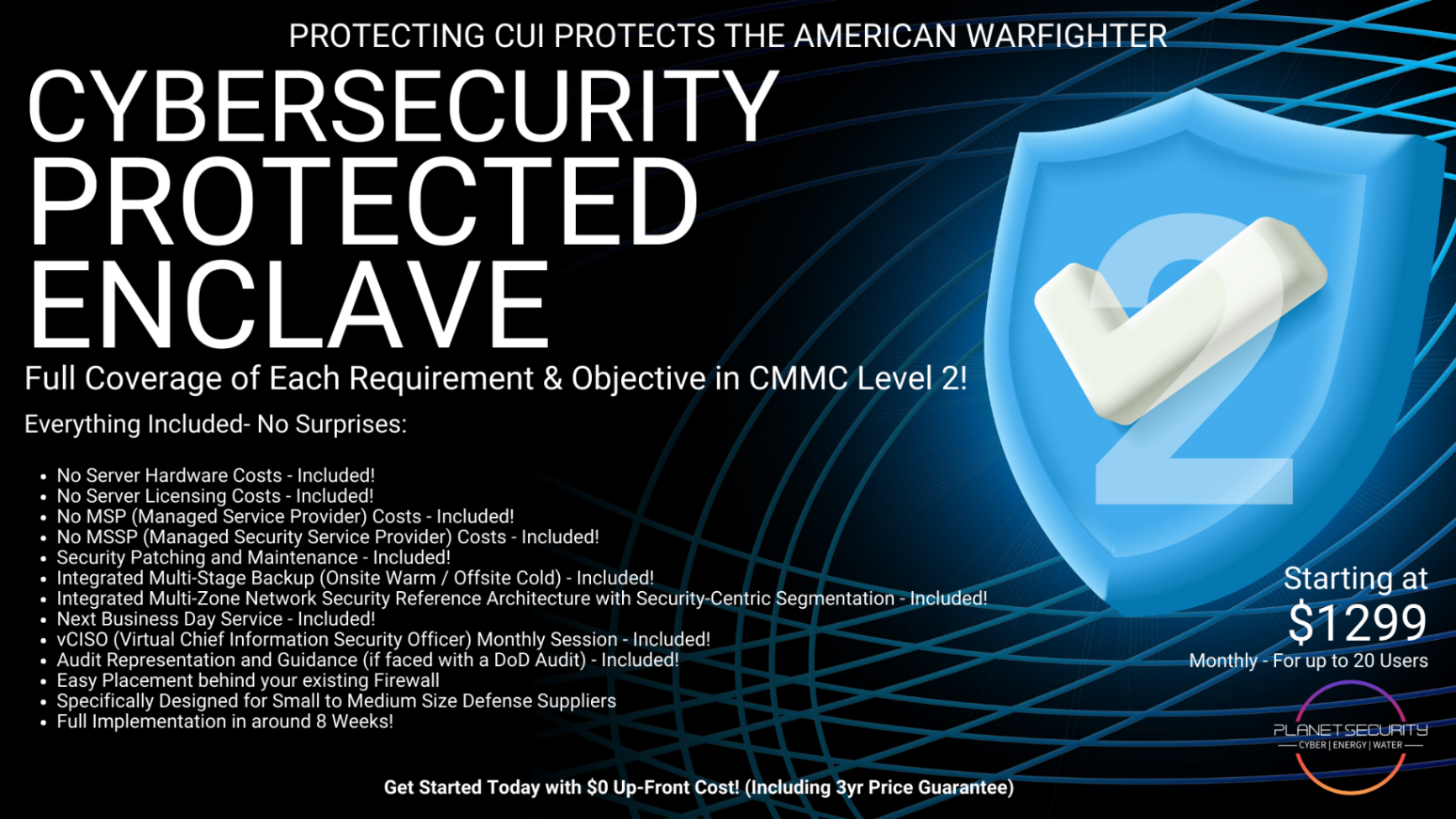
CPE Level 2 flips the script. For a predictable monthly cost starting at $1,299 for up to 20 users, you get enterprise-grade security operations without the enterprise-grade headcount.
And here's the kicker: our managed operations are specifically designed for CMMC compliance. We're not a generic managed security provider trying to figure out what the DoD wants. We built CPE Level 2 from the ground up to meet CMMC 2.0 Level 2 requirements: and we operate it the same way.

Stop the Madness. Start Operating.
The whack-a-mole approach to IT compliance is exhausting, expensive, and ultimately unsustainable. You can keep chasing problems as they pop up, or you can hand the mallet to someone who actually enjoys the game.
Planet Security's CPE Level 2 gives you complete CMMC 2.0 Level 2 compliance with managed operations that keep you compliant day after day, month after month, year after year.
Ready to stop playing games with your compliance? Let's talk about how CPE Level 2 can transform your security operations from a constant headache into a competitive advantage.
| planetsecurity.net | [QR CODE PLACEHOLDER] |
|---|
