Picture this: Your phone rings on a Tuesday morning. It's the Defense Contract Management Agency, and they want to schedule your CMMC audit. Your stomach drops. You've been dreading this call for months.
If you're like most small defense suppliers, you've probably been scrambling to piece together CMMC compliance with whatever tools and vendors you could find. Maybe you bought some software here, hired a consultant there, and crossed your fingers that everything would work together when audit time came.
That approach is about to bite you.
The Reality Check: What Happens When Auditors Show Up
Here's what most small suppliers don't realize until it's too late. When CMMC auditors walk through your door, they're not just checking boxes on a compliance checklist. They're looking for comprehensive, integrated security that covers every single requirement and objective.
They want to see your access controls, incident response procedures, system monitoring, data encryption, network segmentation, and about 100 other technical requirements – all working together seamlessly.
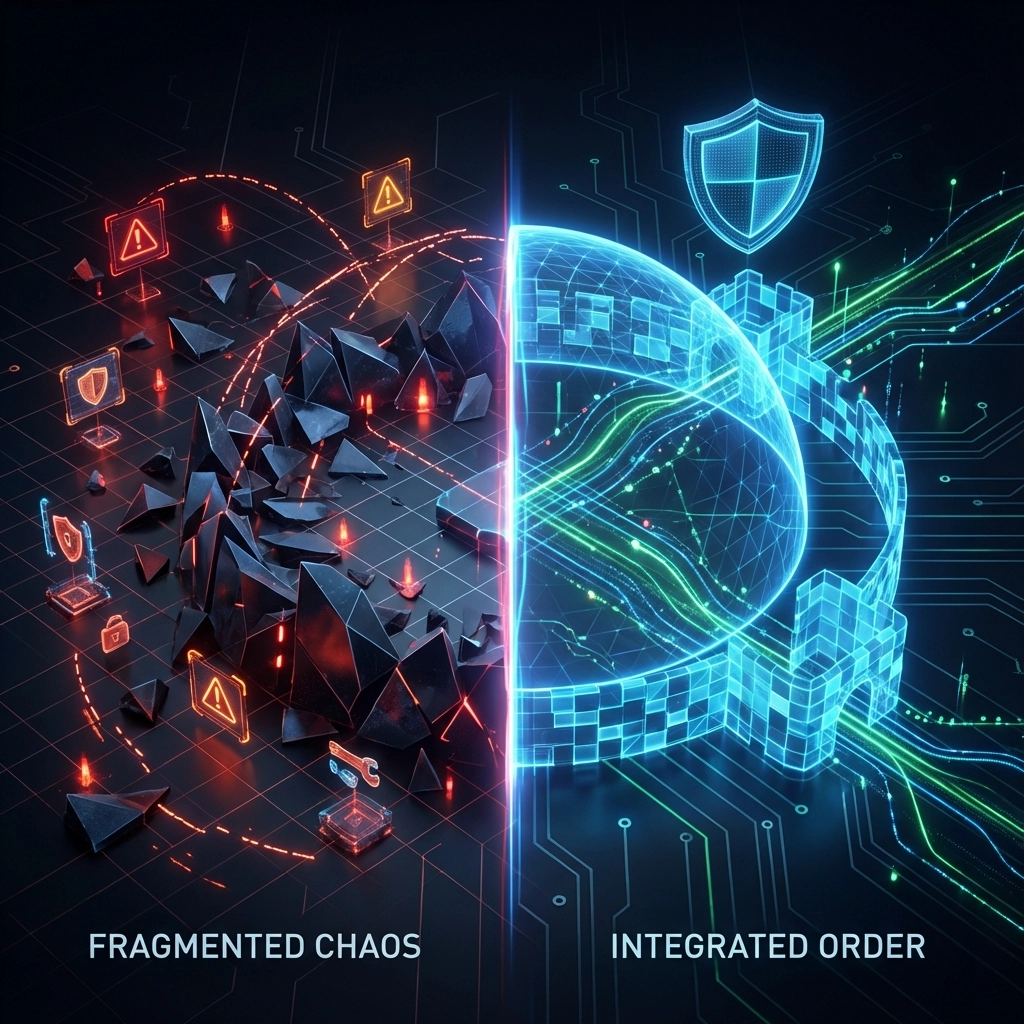
If you've cobbled together your compliance from different vendors and tools, you're in for a rough ride. Auditors will spot gaps, inconsistencies, and missing pieces faster than you can explain them away.

Why Piecing Together CMMC Compliance Is a Recipe for Disaster
Most small defense suppliers make the same mistake. They think they can save money by buying individual security tools and services from different vendors.
Here's what typically happens:
- You buy antivirus software from one vendor
- Network monitoring from another
- Backup services from a third company
- Encryption tools from somewhere else
- Hire a consultant to write your policies
- Contract with an MSP for basic IT support
Then audit time comes, and you discover these tools don't talk to each other. Your documentation is scattered across multiple systems. Half your security controls aren't properly configured. Your incident response plan references systems you don't even use anymore.
The auditor takes one look at this mess and fails you on the spot.
Enter CPE Level 2: The All-in-One Game Changer
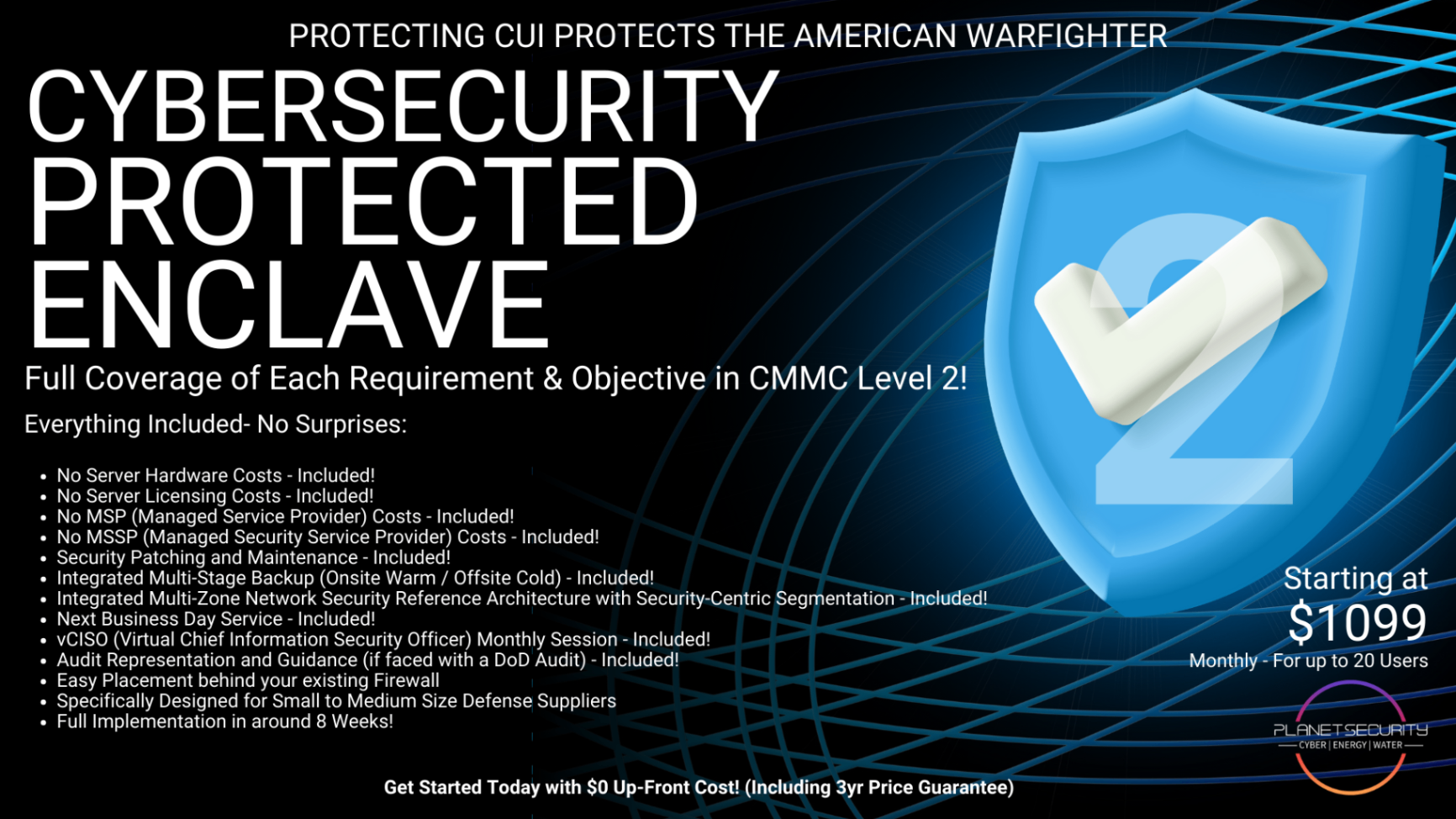
This is exactly why Planet Security created our CPE Level 2 solution. Instead of forcing small suppliers to become cybersecurity experts overnight, we provide everything you need in one integrated package.
CPE Level 2 isn't just another security tool. It's a complete cybersecurity ecosystem designed specifically for CMMC compliance.

What Makes CPE Level 2 Different
100% CMMC Coverage, Zero Guesswork
Our CPE Level 2 covers every single CMMC requirement and objective. Not 90%. Not "most of them." All of them.
When auditors ask about access controls, system monitoring, incident response, or any other CMMC requirement, you point them to your CPE Level 2 system. Everything is documented, configured, and ready for inspection.
Integrated Documentation That Actually Makes Sense
Instead of hunting through multiple vendor portals and spreadsheets for your compliance documentation, everything lives in one place. Your policies, procedures, system configurations, and audit trails are all automatically generated and maintained by the system.
Real-Time Compliance Monitoring
Unlike traditional security tools that you have to check manually, CPE Level 2 continuously monitors your compliance status. If something drifts out of compliance, you know immediately – not during your audit.
The Economics Make Perfect Sense
Most small suppliers think hiring multiple vendors will save money. They're dead wrong.
By the time you pay for:
- Multiple security software licenses
- Various managed services contracts
- Consultant fees for policies and procedures
- Integration costs to make everything work together
- Remediation costs when things inevitably break
You've spent more than CPE Level 2 costs – and you still don't have comprehensive coverage.
Our CPE Level 2 delivers everything for one predictable monthly cost. No surprise fees, no additional licensing costs, no integration headaches.
What Your Audit Will Actually Look Like
With CPE Level 2, here's what happens when auditors show up:
Day 1: They ask for your system architecture documentation. You pull it up in your CPE Level 2 portal – complete, current, and automatically generated.
Day 2: They want to see your access controls in action. You demonstrate how CPE Level 2 manages user permissions, monitors access attempts, and logs everything automatically.
Day 3: They test your incident response procedures. You show them how CPE Level 2 detected, contained, and documented the last security event – all following CMMC requirements exactly.
Instead of scrambling to explain gaps and inconsistencies, you're demonstrating a cohesive, comprehensive security program that clearly meets every CMMC requirement.
The Technical Advantages That Matter
Network Segmentation Done Right
CPE Level 2 automatically creates proper network segmentation to protect your Controlled Unclassified Information (CUI). No guessing about VLAN configurations or wondering if your segmentation meets CMMC requirements.
Continuous Monitoring and Alerting
While other solutions require manual monitoring, CPE Level 2 watches everything 24/7. Unusual network activity, failed login attempts, system changes – everything is logged, analyzed, and reported automatically.
Backup and Recovery That Works
Most small suppliers learn too late that their backup solution doesn't meet CMMC requirements. CPE Level 2 includes integrated backup and disaster recovery that's specifically designed for CMMC compliance.
Encryption Everywhere
Data encryption isn't optional under CMMC – it's required. CPE Level 2 handles encryption at rest and in transit automatically, with proper key management and documentation.
Beyond Compliance: Real Security Benefits
While CMMC compliance is critical, CPE Level 2 delivers genuine security improvements that protect your business:
- Advanced threat detection that spots attacks other tools miss
- Automated patch management that keeps systems secure without disrupting operations
- Identity and access management that scales with your business
- Incident response capabilities that minimize damage when attacks occur
Making the Switch Is Easier Than You Think
We know changing security providers feels risky. That's why CPE Level 2 migration is designed to be seamless:
Week 1-2: Assessment and planning
Week 3-4: System deployment and configuration
Week 5-6: Data migration and user training
Week 7-8: Testing and audit readiness verification
In two months, you go from compliance chaos to audit-ready confidence.

The Bottom Line for Small Defense Suppliers
CMMC audits are coming whether you're ready or not. You can keep trying to piece together compliance from multiple vendors, hoping everything works when auditors show up. Or you can deploy a proven, comprehensive solution that covers everything.
CPE Level 2 isn't just about passing your audit – though it absolutely ensures you will. It's about transforming your security posture from a compliance burden into a competitive advantage.
Your competitors are still scrambling with outdated approaches. You could be ready for anything.
Ready to Stop Worrying About Your CMMC Audit?
The question isn't whether you'll face a CMMC audit. The question is whether you'll pass it.
With CPE Level 2, the answer is absolutely yes.
planetsecurity.net | QR Code for CPE Level 2
