Let's be real for a second. When most defense suppliers hear "network compliance for CMMC," they immediately picture sleepless nights, tangled cables, and a headache that just won't quit. And honestly? That reaction makes total sense.
Network security for CMMC 2.0 Level 2 is complicated. There's no sugarcoating it. But here's the thing, it doesn't have to be your nightmare to solve. That's exactly why we built a better way.
The Firewall Myth: Why It's Not Enough
Here's a mistake we see all the time: a company buys a shiny new firewall, slaps it on the network perimeter, and calls it a day. Box checked. Network secured. CMMC ready.
Not even close.
A firewall is absolutely part of the equation, don't get us wrong. But thinking a firewall alone will get you through a CMMC Level 2 assessment is like thinking a deadbolt on your front door makes your entire house burglar-proof. What about the windows? The garage? The back patio slider that doesn't lock properly?
Network security for CMMC is about the whole architecture, not just one component. You need:
- Proper network segmentation to isolate CUI (Controlled Unclassified Information)
- Access controls that enforce least privilege
- Encrypted communications across all sensitive data flows
- Monitoring and logging that actually catches anomalies
- Secure configurations on every device touching your network
- Boundary protection that goes way beyond a basic firewall
And that's just scratching the surface. CMMC 2.0 Level 2 pulls from 110 security controls outlined in NIST SP 800-171. A significant chunk of those controls directly relate to how your network is designed, configured, and monitored.
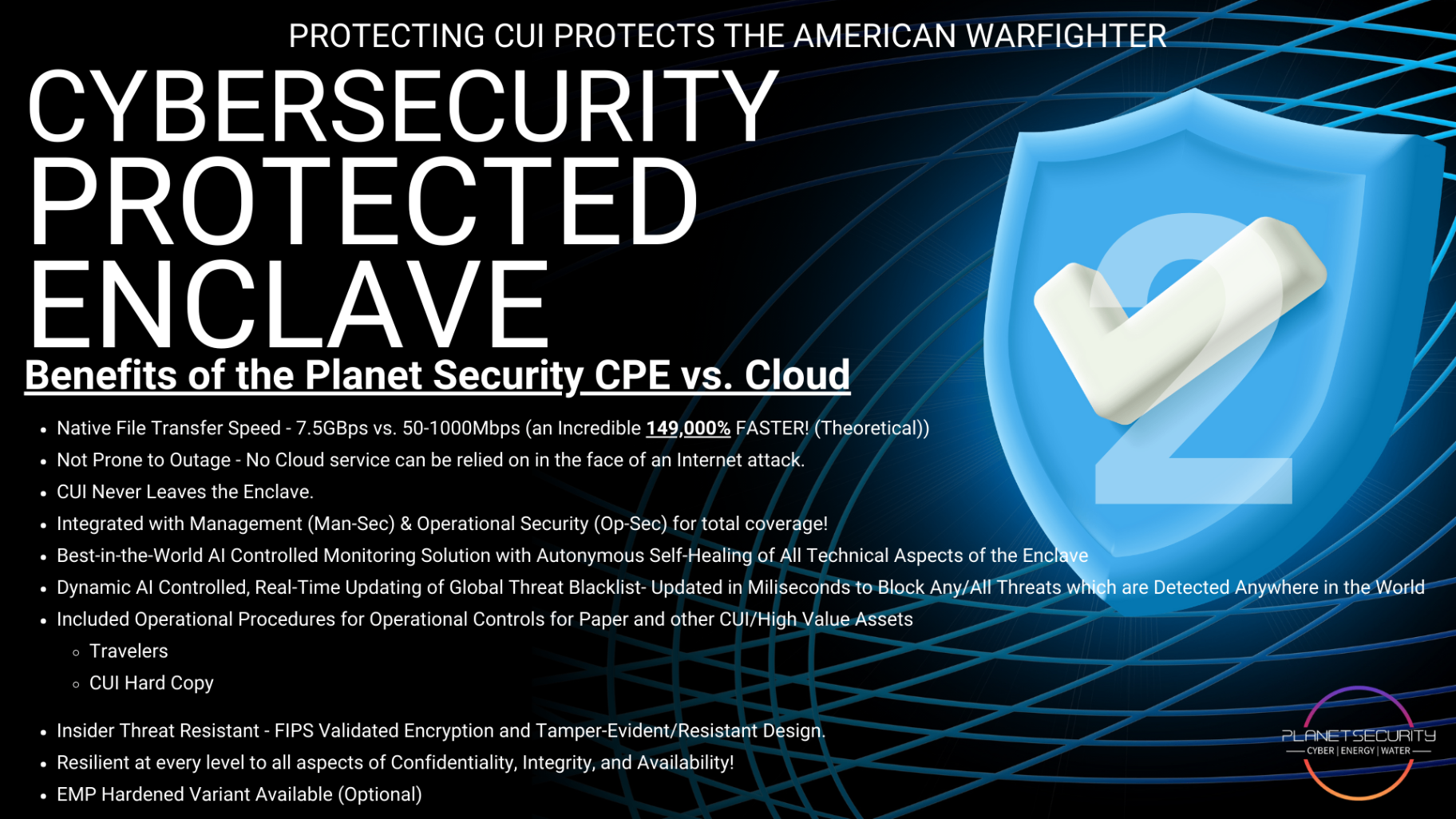
What Is a Security Reference Architecture (And Why Should You Care)?
Okay, so if a firewall isn't enough, what's the answer? A Security Reference Architecture (SRA).
Think of an SRA as the master blueprint for your entire network security setup. It's a pre-designed, validated framework that tells you exactly:
- How your network should be segmented
- Where your security controls need to be placed
- How data should flow between systems
- What configurations are required on each device
- How users should authenticate and access resources
An SRA isn't something you dream up on a whiteboard during a Monday morning meeting. It's a battle-tested design built specifically to meet compliance requirements: in this case, CMMC 2.0 Level 2.
Here's the problem: most small and medium defense suppliers don't have the expertise, time, or budget to develop their own Security Reference Architecture from scratch. And even if they did, they'd still need to implement it, test it, document it, and prove it works during an assessment.
That's a massive lift. And it's exactly where most CMMC journeys go off the rails.
Enter CPE Level 2: Your Pre-Configured Security Reference Architecture
This is where CPE Level 2 changes everything.
CPE Level 2 isn't just a product: it's a complete solution that includes a pre-configured Security Reference Architecture designed specifically for CMMC 2.0 Level 2 compliance. We've done the heavy lifting so you don't have to.
When you deploy CPE Level 2, you're not just getting hardware and software. You're getting:
- A fully designed network architecture that meets all 110 NIST SP 800-171 controls
- Pre-configured network segmentation that properly isolates your CUI environment
- Security-enabled firewalls with configurations validated against CMMC requirements
- Built-in access controls enforcing zero-trust principles
- Encrypted communications for all sensitive data flows
- Continuous monitoring and logging that satisfies assessment requirements
- Complete documentation ready for your C3PAO assessment

No guesswork. No sleepless nights. No hiring a team of network architects.
The Security Reference Architecture inside CPE Level 2 has been refined across hundreds of implementations. We know exactly what assessors are looking for, and we've built it right into the solution.
The Real Benefits of a Pre-Configured Architecture
Let's break down why this matters for your business:
1. Massive Time Savings
Designing a compliant network architecture from scratch can take months. Testing it, tweaking it, and documenting it takes even longer. With CPE Level 2, you can be audit-ready in as little as 4 weeks.
That's not a typo. Four weeks from kickoff to compliance-ready.
2. Dramatically Lower Costs
Hiring network security architects, compliance consultants, and implementation specialists adds up fast. We're talking hundreds of thousands of dollars for many organizations. CPE Level 2 delivers enterprise-grade architecture at a fraction of that cost.
3. Reduced Risk of Getting It Wrong
Here's the scary truth: one misconfigured network segment can sink your entire assessment. Our Security Reference Architecture has been validated and proven across real-world CMMC assessments. You're not gambling on whether your design will pass: you're deploying a known winner.
4. Ongoing Compliance Without the Headache
Network compliance isn't a one-and-done deal. Configurations drift. New threats emerge. Requirements evolve. CPE Level 2 includes continuous technical compliance monitoring so your architecture stays compliant long after deployment.
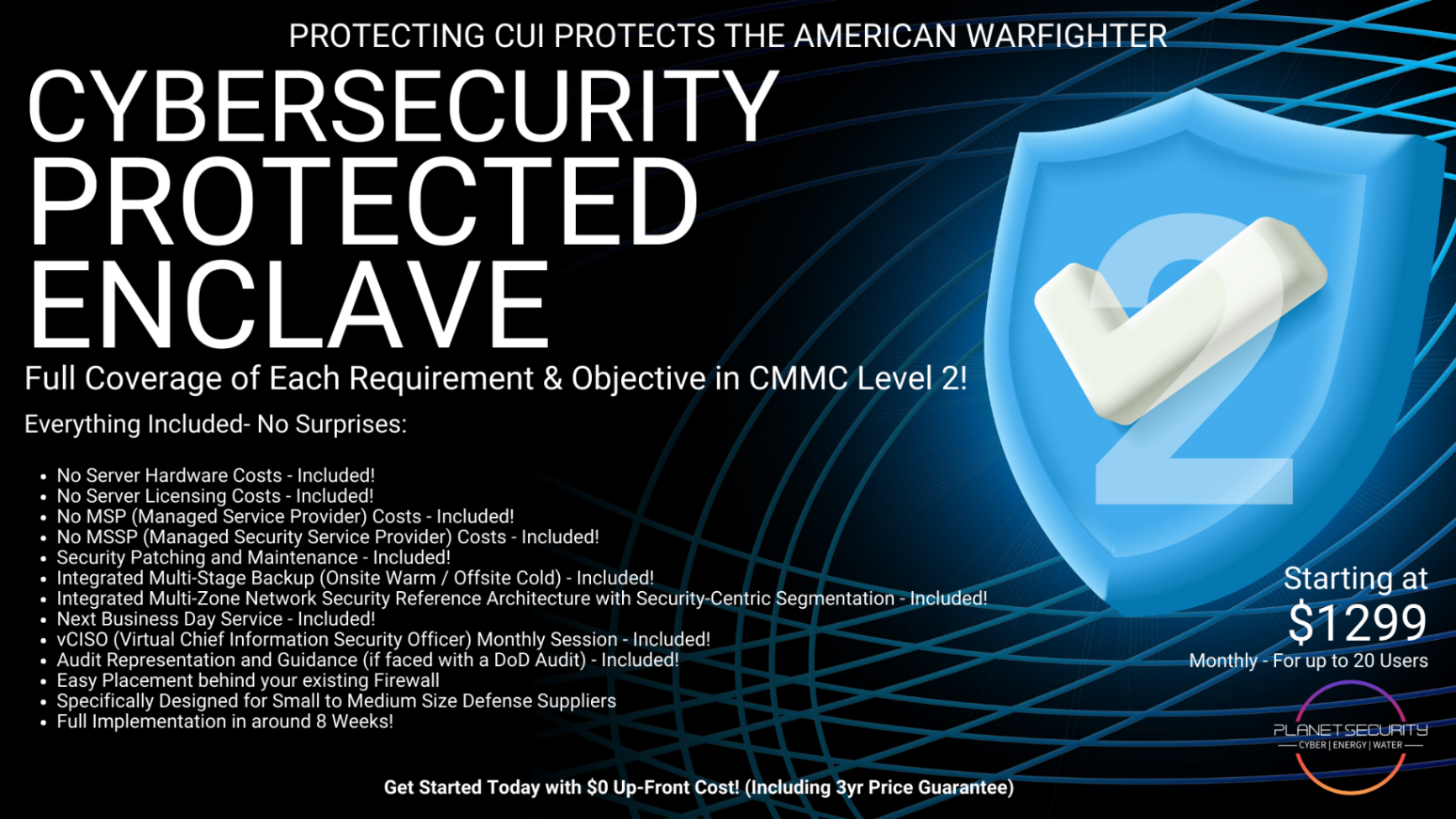
What's Actually Included in the CPE Level 2 Architecture?
Let's get specific. When we say "pre-configured Security Reference Architecture," here's what that actually means:
Network Segmentation:
- Dedicated CUI enclave isolated from general business network
- Properly configured VLANs and subnets
- Controlled data flows between segments
Boundary Protection:
- Security Reference Architecture-enabled firewalls with CMMC-compliant rule sets
- Intrusion detection and prevention
- Secure remote access configurations
Access Controls:
- Role-based access enforcement
- Multi-factor authentication integration
- Least privilege configurations
Encryption:
- FIPS 140-2 validated encryption for data at rest and in transit
- Secure communication protocols across all network segments
Monitoring & Logging:
- Centralized log collection and analysis
- Real-time alerting for security events
- Audit trail documentation for assessments
And that's just the networking piece. CPE Level 2 covers all 110 controls: technical, operational, and personnel security included.
Stop Building From Scratch
Here's the bottom line: you shouldn't have to become a network security expert just to keep your DoD contracts.
The Security Reference Architecture inside CPE Level 2 represents years of expertise, countless hours of design work, and real-world validation across actual CMMC assessments. It's the architecture your business needs, ready to deploy.
No guesswork. No nightmare. Just compliance.
If you're tired of staring at network diagrams wondering if you're doing it right, it's time for a conversation. Let us show you how CPE Level 2 takes the networking nightmare off your plate: completely.

Ready to See the Difference?
Get started today. Reach out to our team and discover why defense suppliers across the country are choosing CPE Level 2 as their path to CMMC compliance.
Your network doesn't have to be a nightmare. We've already solved it for you.
| planetsecurity.net | [QR CODE] |
|---|
