Let's get one thing straight right out of the gate: CMMC compliance isn't a finish line you cross once and forget about. If you're treating your cybersecurity certification like a one-time checkbox exercise, you're setting yourself up for a world of pain down the road.
The Department of Defense didn't create CMMC 2.0 so you could pass an assessment, dust off your hands, and call it a day. Nope. They built it because cyber threats are relentless, sophisticated, and evolving every single day. Your compliance needs to keep pace: and that means continuous monitoring is your new best friend.
The "One and Done" Myth
Here's a scenario we see all the time: A defense supplier scrambles to get their systems in order, passes their CMMC assessment, and then… relaxes. The champagne comes out, everyone pats themselves on the back, and security slowly drifts back to "business as usual."
Big mistake.
Threat actors don't take vacations. They don't care that you passed an audit six months ago. They're probing your network right now, looking for that one misconfigured firewall rule, that one unpatched vulnerability, that one employee who clicked a phishing link.
CMMC isn't a sprint: it's a marathon. You have to prove you're secure every single day. And honestly? That's exactly how it should be when you're handling Controlled Unclassified Information (CUI) for the Department of Defense.
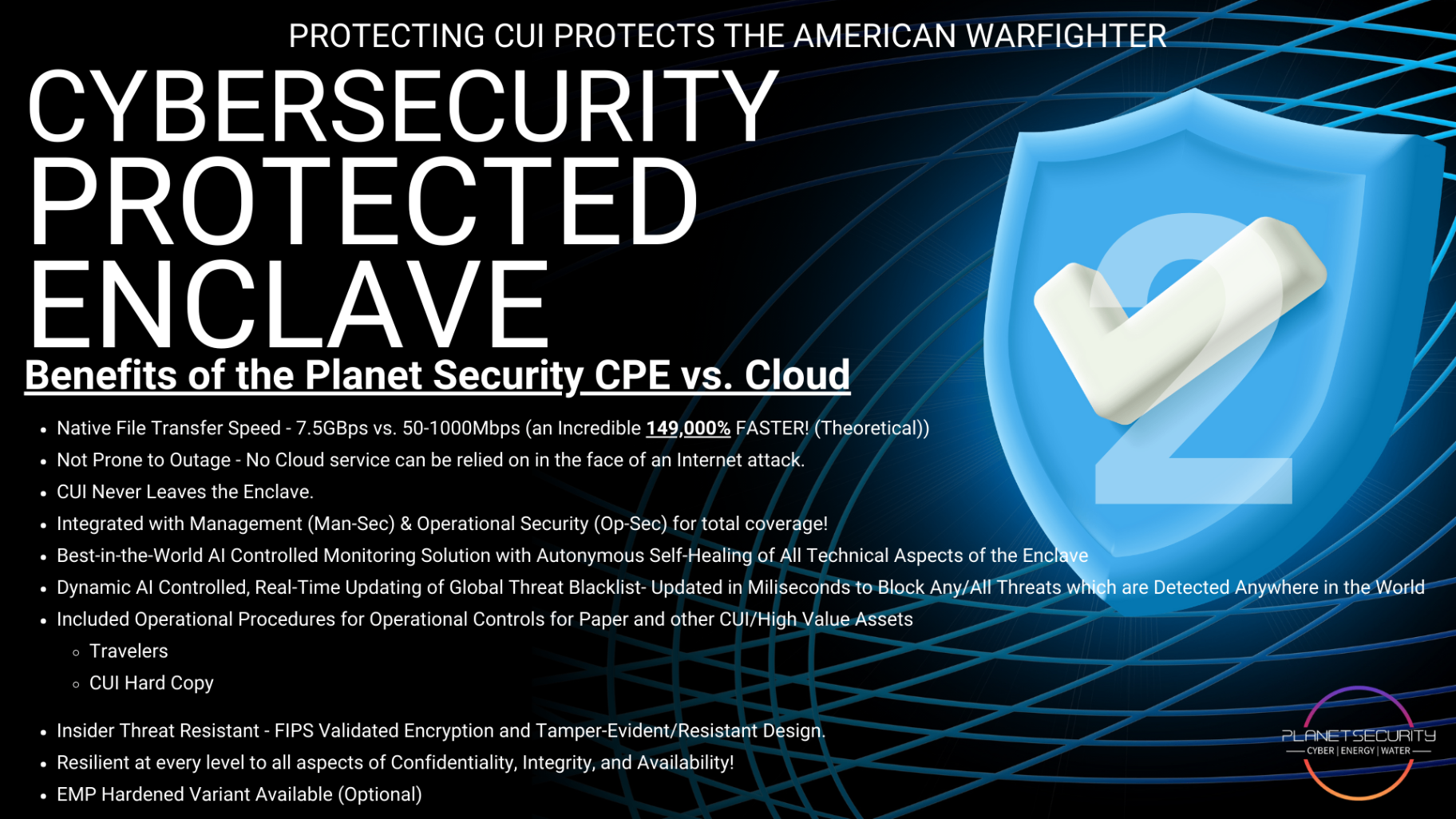
What Continuous Monitoring Actually Means
So what does "continuous monitoring" look like in practice? It's not just running an antivirus scan once a week and hoping for the best. Real continuous monitoring is an always-on, always-watching approach to your security posture.
Here's what it involves:
- Real-time analysis of network traffic, system logs, and user activities
- Proactive threat detection that identifies attacks before they cause damage
- Vulnerability management that catches weaknesses before bad actors do
- Compliance verification that ensures your controls are working as intended
- Incident response readiness so you can act fast when something goes sideways
The goal is simple: maintain ongoing awareness of your security status, vulnerabilities, and threats. This isn't about paranoia: it's about operational resilience.
The SIEM Problem (And Why Business Owners Lose Sleep)
At the heart of continuous monitoring sits your SIEM: Security Information and Event Management. This is the system that collects logs from across your network, analyzes them for suspicious activity, and alerts you when something's wrong.
Sounds great, right? In theory, absolutely.
In practice? SIEM management is a nightmare for small and medium-sized businesses.
Here's the reality:
- Log volume is overwhelming. We're talking thousands: sometimes millions: of events per day. Who's going to sift through all that?
- Alert fatigue is real. Too many false positives mean your team starts ignoring alerts. Then the real attack slips through.
- Expertise is expensive. You need trained security analysts working around the clock. For a 50-person defense supplier? That's just not realistic.
- Compliance reporting is tedious. CMMC assessors want documentation. Lots of it. Generating compliant reports from raw SIEM data is a full-time job.
This is why business owners stay up at night worrying about logs. You know you need continuous monitoring to stay compliant, but actually implementing it feels impossible.

Enter CPE Level 2: Continuous Monitoring on Autopilot
This is where CPE Level 2 changes everything.
Our Cybersecurity Protected Enclave doesn't just help you pass your initial CMMC assessment: it keeps you compliant through automated, continuous monitoring and reporting.
Here's how CPE Level 2 handles the heavy lifting:
Automated SIEM Monitoring
CPE Level 2 includes integrated SIEM capabilities that run 24/7/365. All network traffic, system logs, and user activities within your enclave are continuously collected, analyzed, and stored. Our system handles the log aggregation, correlation, and analysis: so you don't have to.
Intelligent Alerting
Forget alert fatigue. CPE Level 2 uses intelligent threat detection that filters out the noise and escalates only the events that matter. When there's a genuine security concern, you'll know about it immediately.
Compliance-Ready Reporting
Need to demonstrate continuous monitoring for your CMMC assessor? CPE Level 2 generates audit-ready reports automatically. No more scrambling to compile evidence. No more late nights building spreadsheets. The documentation you need is ready when you need it.
Global Dynamic Threat Blacklisting
Our latest version includes global dynamic threat blacklisting that updates in real-time. When a new threat is identified anywhere in the world, your enclave is protected automatically. This is proactive defense at its finest.
The Sustainment Phase: Where Compliance Lives
CMMC implementation isn't just about scoping, planning, and passing your assessment. The sustainment phase: the part that comes after certification: is where your compliance program actually lives.
Think about it this way:
- Scoping – Figure out what systems handle CUI
- Planning – Develop your implementation roadmap
- Implementation – Put controls in place
- Assessment – Pass your CMMC evaluation
- Sustainment – Maintain compliance forever
That last phase? It's not optional, and it never ends.
CPE Level 2 is specifically designed to make sustainment sustainable. We've built continuous monitoring into the foundation of the enclave, not bolted it on as an afterthought.

Why This Matters for Your Business
Let's talk brass tacks. Why should you care about continuous monitoring beyond "the DoD requires it"?
Protect Your Contracts
Lose your CMMC certification, and you lose your ability to bid on DoD contracts. It's that simple. Continuous monitoring helps you avoid compliance violations that could tank your certification status.
Reduce Risk Exposure
A data breach involving CUI isn't just embarrassing: it's potentially catastrophic. We're talking legal liability, reputational damage, and possibly being barred from future government work. Continuous monitoring catches threats before they become breaches.
Sleep Better at Night
Seriously. When you know your SIEM is being managed by professionals, your logs are being analyzed around the clock, and your compliance reports are generating automatically: you can actually focus on running your business instead of worrying about cybersecurity.
Stay Ahead of Evolving Threats
Threat actors are constantly increasing both the sophistication and frequency of their attacks. A static security posture from six months ago is already outdated. Continuous monitoring keeps your defenses current and adaptive.
The Bottom Line
CMMC compliance isn't a destination: it's a journey. You have to prove you're secure every day, not just on assessment day.
For small and medium-sized defense suppliers, building and maintaining a continuous monitoring capability in-house is expensive, complex, and often unrealistic. That's exactly why we built CPE Level 2 to handle it for you.
Automated SIEM monitoring. Intelligent threat detection. Compliance-ready reporting. Global threat updates. All included.
Stop treating CMMC like a sprint. Start running the marathon with the right partner by your side.
Ready to see how CPE Level 2 makes continuous monitoring effortless? Visit our CPE Level 2 page to learn more about how we're helping defense suppliers maintain compliance: every single day.
| planetsecurity.net | [QR CODE] |
|---|
